In HR reporting, a single data leak can mean more than a privacy issue. It is a trust issue. A recent report found that the average cost of a data breach now exceeds USD 5 million. HR systems are vulnerable because they contain the highest concentration of personal and sensitive information inside an organization. That number would rise even further when the breach involves salary or health-related fields.
Yet despite this level of exposure, most organizations still equate “security” with login credentials, MFA prompts, or IT access checklists. Necessary, yes. Sufficient, no. Because the real protection in HR reporting does not live on the login screen. It lives deep inside the data architecture.
This blog unpacks what secure HR reporting actually looks like behind the scenes.
How enterprise systems govern who can view which rows and which columns.
How audit trails capture every action.
Why governance architecture matters as much as encryption.
And why custom BI setups, when not designed with HR’s sensitivity in mind, often open quiet but serious gaps.
Because in HR, who sees what is just as important as who logs in.
Beyond Logins: The Layers of HR Data Security
Most HR teams think of security as authentication. But in reporting, authentication is only the first lock on a much larger vault. Enterprise-grade HR systems protect data through three distinct layers. Each one solves a different problem, and together they create the only reliable foundation for secure reporting.The Access Layer: Who Can Enter
This layer answers the simplest question: Is this person allowed into the system at all? It covers technologies like:- Secure Single Sign-On
- Multi-Factor Authentication
- LDAP and Active Directory integrations
- Identity federation and lifecycle management for joiners, movers, and leavers
The Data Layer: What They Can See
This is where real HR reporting security begins. The data layer controls visibility, not access. It determines exactly which rows and columns appear on screen for each user. Two mechanisms power this:- Role-based permissions to align access with HR, payroll, manager, and executive responsibilities
- Row- and column-level filtering to restrict visibility based on geography, business unit, hierarchy, sensitivity, or regulatory boundaries
- An HRBP in EMEA sees only EMEA employee data.
- A payroll administrator sees compensation fields but not performance ratings.
- A line manager sees only direct and indirect reports.
The Audit Layer: What They Did
Security is not complete unless every action is traceable. The audit layer provides:- Immutable logs of report views, downloads, and data exports
- Version histories of dashboards and data models
- Timestamped trails for compliance checks and investigations
Row-Level and Column-Level Security: The Heart of Confidential Reporting
Once a user enters the system, the question shifts from “Can they access?” to “What exactly should they see?” This is where precision access begins. In HR reporting, two security mechanisms make that possible: row-level filtering and column-level filtering.
Row-Level Security: Filtering by Context
Row-level security controls which records a user can view.
It filters data based on attributes such as:
- Region or geography
- Business unit
- Department
- Manager hierarchy
- Employee group or classification
Example:
A Human Resources Business Partner supporting EMEA should only see EMEA employee data, even if the report template covers the entire global workforce.
Row-level controls prevent cross-regional exposure, which is essential for frameworks like GDPR where data residency and data minimization rules apply.
Column-Level Security: Protecting Sensitive Fields
Column-level security restricts which fields a user can view inside a record.
This protects sensitive information such as:
- Salary and total compensation
- Age or birth date
- Health or leave data
- Performance ratings
- National identifiers
Example:
A payroll administrator may need visibility into compensation fields, but not performance ratings.
A line manager may view attendance trends but should never see medical leave codes.
Column-level controls are central to compliance obligations under HIPAA in the United States and PDP in India, where access to sensitive fields must be explicitly controlled and logged.
True compliance does not come from policy documents.
It comes from data design.
Systems that enforce visibility at the row and column level reduce risk more effectively than external rules or manual oversight.
What Custom BI Setups Often Miss
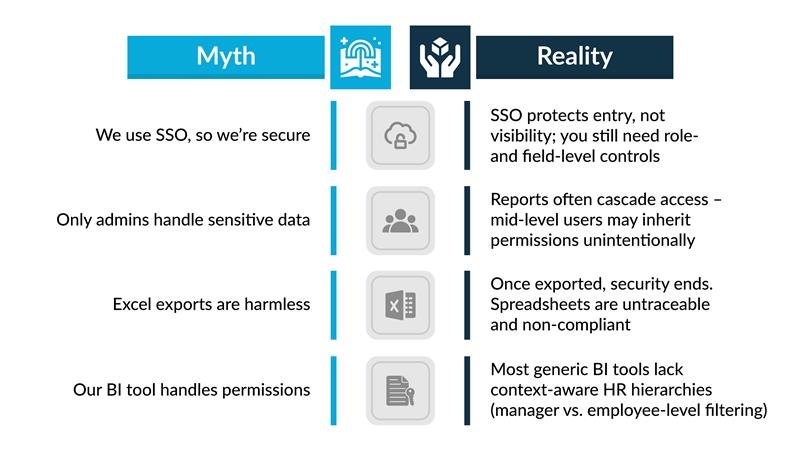
Custom BI environments give teams flexibility, but that flexibility comes with blind spots that most HR and IT teams underestimate. Unlike enterprise-grade HR platforms, homegrown or loosely governed BI setups lack built-in guardrails. The result is a reporting environment that looks functional on the surface but quietly exposes sensitive data underneath. Here are the risks that appear most often:- Overly broad access groups: Many custom BI implementations rely on large, catch-all permission groups such as “HR_ALL” or “Manager_ALL.” Once someone is added to these groups, they inherit visibility to data far beyond their role. This is one of the most common pathways to accidental exposure.
- Excel and sheets exports break containment: The moment data leaves a secure system and lands in Excel, Sheets, or a shared drive, all protections disappear. Files get copied, forwarded, downloaded, and stored in personal folders, turning controlled data into an uncontrolled asset.
- Ad-hoc joins reveal unintended PII: Custom BI tools make it easy to blend datasets for “quick insights.” But those joins often pull fields together in ways no HR system would ever allow, accidentally combining identifiers, compensation data, or medical leave codes into a single report.
- No audit logs means zero traceability: When a breach or policy violation occurs, custom BI tools rarely provide immutable logs at the field or export level. Without a trace, organizations cannot answer the most critical compliance question: Who viewed or downloaded what, and when?
How Enterprise Platforms Enforce Security by Design
Enterprise HR reporting platforms work differently from custom BI environments. Instead of relying on manual rules, spreadsheet governance, or one-off permissions, they build protection directly into the reporting architecture. The result is a system where every query, every field, and every export passes through a controlled security pipeline.
Here are the safeguards that define enterprise-grade design:
Dynamic row-level filtering tied to hierarchy:
Enterprise systems map users to the organization automatically.
Managers see only their teams. HRBPs see only their regions. Payroll sees only their scope.
There is no manual configuration and no guesswork.
Every refresh applies the right filters without exception.
Centralized permission management across roles:
Enterprise platforms store all visibility rules in a single governance layer.
No scattered report-level permissions. No ad-hoc exceptions.
When a user changes roles, their access updates instantly, reducing exposure from outdated permissions.
Immutable audit logs with complete download tracking:
Every action is captured: views, filters, exports, downloads, and access changes.
Logs cannot be modified, erased, or bypassed.
When auditors ask who saw salary data or when a file was exported, enterprise systems give answers in seconds.
Encryption applied at rest and in transit:
Data stays protected whether it is stored, refreshed, transmitted, or queried.
Secure channels prevent interception, and encrypted storage reduces the risk of internal misuse.
Automatic, secure data refresh from certified connectors:
Enterprise platforms avoid manual extracts, CSV uploads, or DIY joins.
Data flows through governed connectors that maintain schema, validate fields, and enforce security with every pull.
No accidental blending. No unintended PII exposure. No uncontrolled spreadsheets.
In enterprise systems, security is not an add-on. It is the default. Every report becomes safe by design rather than safe by chance.
Common Misconceptions About HR Reporting Security
The Compliance Connection: Why Reporting Security = Regulatory Readiness
Every major data privacy law has the same underlying expectation: organizations must be able to prove control over their HR data. GDPR requires documented access trails. HIPAA demands protection of health-related fields. SOX audits revolve around integrity, traceability, and evidence. PDP in India reinforces data minimization and strict visibility limits. And across all of them, HR data sits squarely in the highest-risk category.
This is where reporting architecture becomes central to compliance. When systems capture and store every report view, filter change, or export with immutable timestamps, investigators no longer need to reconstruct events manually. When sensitive fields such as compensation, identifiers, age, or medical leave codes are segregated at the column level, auditors immediately see that the organization has intentionally restricted exposure. And when role-based access aligns to real org structures and hierarchy logic, it becomes easy to demonstrate least-privilege access.
In short, compliance becomes simpler when visibility is engineered into the reporting system rather than enforced through policies or manual oversight. The more audit-friendly the design, the fewer surprises during reviews, investigations, or regulatory checks.
The Takeaway: Trust Is Built in the Backend
Security is the confidence layer of HR analytics, not just a checkbox item.
The organizations that get reporting right are the ones that treat security as part of the data foundation, not a final review step. And that foundation starts with clarity on who sees what, how access is enforced, and how every action is recorded.
Before scaling any HR reporting or analytics initiative, take a moment to:
- Review who sees what in your current HR dashboards.
- Check whether role-based filtering and export restrictions are configured correctly.
- Ask vendors how audit trails, download logs, and field-level permissions are maintained.
SplashBI embeds security down to the column level, giving HR leaders confidence without compromise.
Request a SplashBI demo to see how secure HR reporting really works.

Ragu Veeraraghavan
VP of Analytics, SplashBI
Ragu Veeraraghavan brings deep expertise in people analytics and workforce strategy. At SplashBI, he leads analytics innovation and customer advisory, shaping product roadmaps and cloud data architecture to help organizations gain maximum value from prebuilt KPIs, predictive models, and real-time insights. With deep expertise in the Oracle ecosystem and strategic vision in business intelligence solutions, he strengthens the platform’s ability to deliver scalable, high-impact analytics.
Ragu engages closely with HR and business leaders across industries – his perspective bridges product capabilities with the pressing needs of HR leaders navigating today’s fast-changing talent landscape.