Inside most enterprises, data security looks strong. ERP, HR, and CRM systems enforce role-based access. Permissions are defined. Audit trails exist. Access is controlled and documented. On paper, everything appears secure.
This creates an illusion of safety.
The failure mode rarely begins inside the source system. It begins after extraction. The moment data is exported, combined, modeled, or shared, it starts moving beyond the boundaries where those controls were originally enforced.
Governance risk does not grow with storage. It grows with movement.
As analytics scales, data travels across tools, teams, and time. Each step introduces new layers of access, identity mapping, and reuse. And that is where controls quietly weaken.
This article walks through the real journey of enterprise data, from export to spreadsheet, and highlights where governance most often breaks before anyone notices.
The Typical Data Journey (And Why It Matters)
Data rarely stays in one place. It travels.
What begins inside a tightly controlled source system often follows a predictable path:
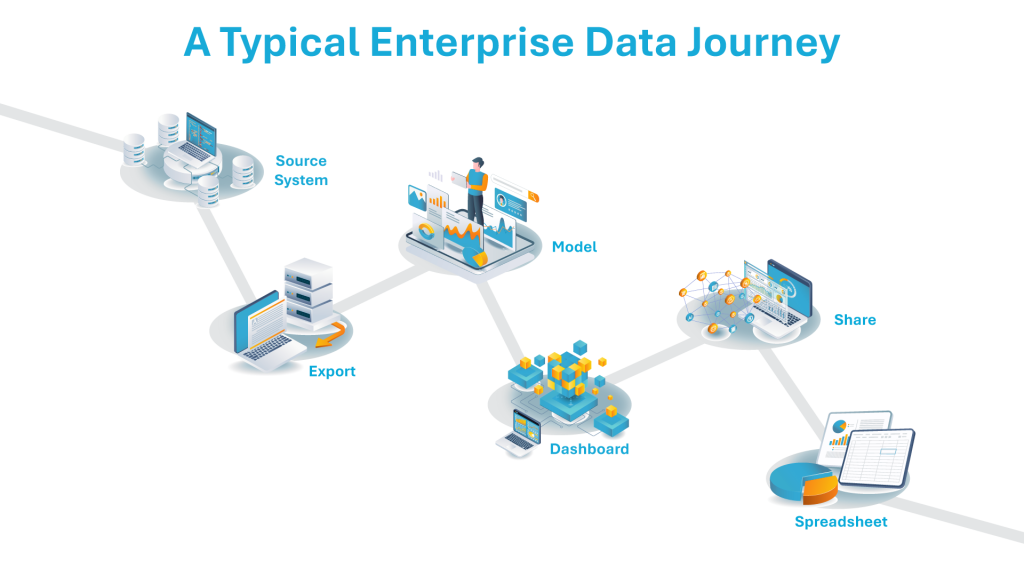
Here’s what that journey usually looks like:
- Export: Data leaves ERP, HR, or CRM systems through extracts, APIs, or scheduled feeds.
- Model: It is transformed and combined in a warehouse or BI layer.
- Dashboard: Visualized for business users in reports and analytics tools.
- Share: Links circulate across teams, departments, and leadership groups.
- Spreadsheet: Data is downloaded for offline analysis, emailed, or saved locally.
Each step increases surface area. Each step introduces governance drift.
Security may be strongest at the source, but most enterprises only govern that first stage rigorously. Once data begins moving, controls become layered, recreated, or bypassed altogether.
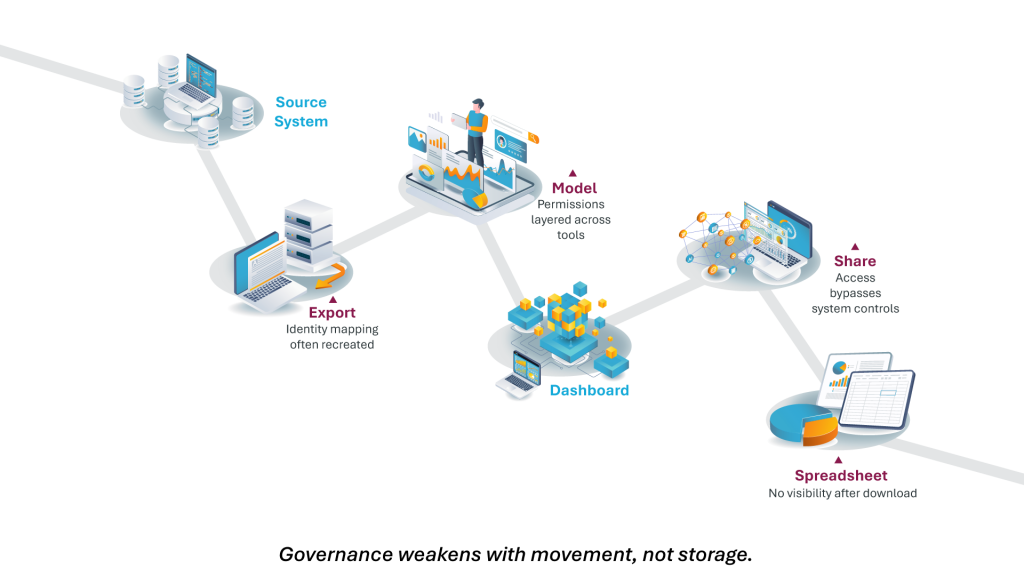
Failure Point #1: Identity Mapping Breaks
User identities do not always travel cleanly across systems.
An ERP role does not automatically map to a BI role. Warehouse permissions are often recreated manually. Analytics tools apply their own access logic. Then dashboards get shared over email, bypassing system-level identity controls altogether.
The result is inconsistent enforcement.
Some users see more than intended. Others lose access unpredictably. Neither scenario triggers a breach alert, but both erode governance.
This happens because security models differ across tools. Governance becomes layered rather than unified. Each system enforces access in isolation, assuming the others will do the same.
Over time, these mismatches accumulate.
Failure Point #2: Role Drift Over Time
Permissions rarely break all at once. They degrade.
Promotions, team changes, and reorganizations are reflected in HR systems, but not always in analytics layers. Access granted “temporarily” to support a project is never revoked. Meanwhile, multiple copies of the same dataset mean multiple permission layers to maintain.
Nothing dramatic happens. There is no breach headline. Just silent overexposure.
This is what makes role drift dangerous. It is incremental. Hard to detect. Easy to rationalize.
Governance does not fail because of one bad decision. It fails because of accumulated small ones.
The core insight is simple. Governance decays with time unless it is automated and actively monitored.
Failure Point #3: Uncontrolled Downloads and Spreadsheets
The biggest risk is not hacking. It is uncontrolled copies.
Dashboards are exported to CSV. Reports are downloaded into Excel. Files are emailed, saved locally, or shared in collaboration tools. These actions are routine and often necessary.
But once data is exported, system-level controls stop applying.
There is no visibility into redistribution. No enforcement of updated permissions. No easy way to revoke access to a spreadsheet that has already circulated.
This is common because business urgency demands flexibility. Teams need offline analysis. Executives want data in familiar formats. Work does not stop at the dashboard.
Control is strongest at the source. It is weakest at the edges.
Failure Point #4: Multi-Source Modeling Without Unified Governance
Combining systems multiplies governance complexity.
HR data is merged with finance. Sales metrics intersect with workforce data. Different sensitivity levels collide in shared models. One tool’s access model may override another’s, creating inconsistencies that are difficult to trace.
Each system may work fine on its own. The risk emerges in integration.
As more data sources are added, audit effort increases dramatically. Proving who had access to what, and under which conditions, becomes harder across environments.
This complexity is often underestimated because integration is framed as a technical task, not a governance one.
The insight is clear. Governance complexity grows exponentially with each additional data source.
Why This Failure Mode Is So Hard to See
This failure mode is difficult to detect because nothing appears broken.
There is no breach. No alert. No dramatic event that signals a problem. Security teams sign off on the source system. Audit logs show controlled access where the data originated.
Meanwhile, control has quietly diffused downstream.
Permissions are recreated in analytics tools. Files are downloaded and shared. Roles drift over time. None of these actions trigger a red flag individually. Together, they weaken governance in ways that are hard to trace back to a single cause.
Governance erosion is incremental, not dramatic. It accumulates through routine behavior.
Which raises the real question.
Before scaling analytics further, what should buyers be asking to make this invisible risk visible?
Questions Buyers Should Ask Before Scaling
The goal is not to create fear. It is to make invisible risk visible before scale amplifies it.
Before expanding analytics usage, buyers should slow down and ask practical governance questions:
-
How is identity preserved when data moves across systems?
Does access follow the user automatically, or is it rebuilt manually in each tool? -
Are permissions inherited or recreated at every layer?>
If recreated, who owns consistency? -
How is stale access detected and removed?>
Is there automated monitoring, or only periodic reviews? -
What happens after data is downloaded?>
Does governance stop at export? -
How are cross-system sensitivities enforced?>
When HR, finance, and sales data combine, whose rules win?
The objective is not paranoia. It is intentional architecture. Enterprises that ask these questions early avoid retrofitting governance later, when scale makes change expensive and painful.
Conclusion: Data Is Not Most Vulnerable at the Source
The most dangerous moment for enterprise data is not when it is stored. It is when it travels.
Source systems are often well governed. Roles are defined. Access is logged. Controls are reviewed. But risk increases with reuse, when data is exported, combined, shared, and downloaded across tools and teams.
Enterprises scaling analytics must design for movement, not just protection at rest. Governance cannot stop at the system boundary. It has to follow data across its lifecycle.
That requires architecture built for cross-system enforcement, unified identity, and consistent control.
Talk to a Governance Expert
Because security protects storage. Governance protects movement.













